Xanthus Security
Attacking Electronic Codebooks
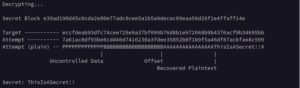
Introduction In this blog post we will discuss weaknesses in the Electronic Codebook (ECB) block cipher mode of operation and demonstrate an attack on a

Introduction In this blog post we will discuss weaknesses in the Electronic Codebook (ECB) block cipher mode of operation and demonstrate an attack on a

“Not content to rest on its scaly laurels, phishing has utilized quarantine to pump up its frequency to being present in 36% of breaches (up

Introduction Any redteamer working in a windows enterprise environment will eventually have to cross paths with Windows Defender and its anti-malware competent AMSI. For an